Sometimes we store items in a storage account and want to restrict the access to certain services or clients. I will demonstrate how to restrict the access to a subnet where a Windows Server 2016 Datacenter VM is running. Service Endpoints in Azure is part of the AZ-303 exam for becoming an Azure Solution Architect.
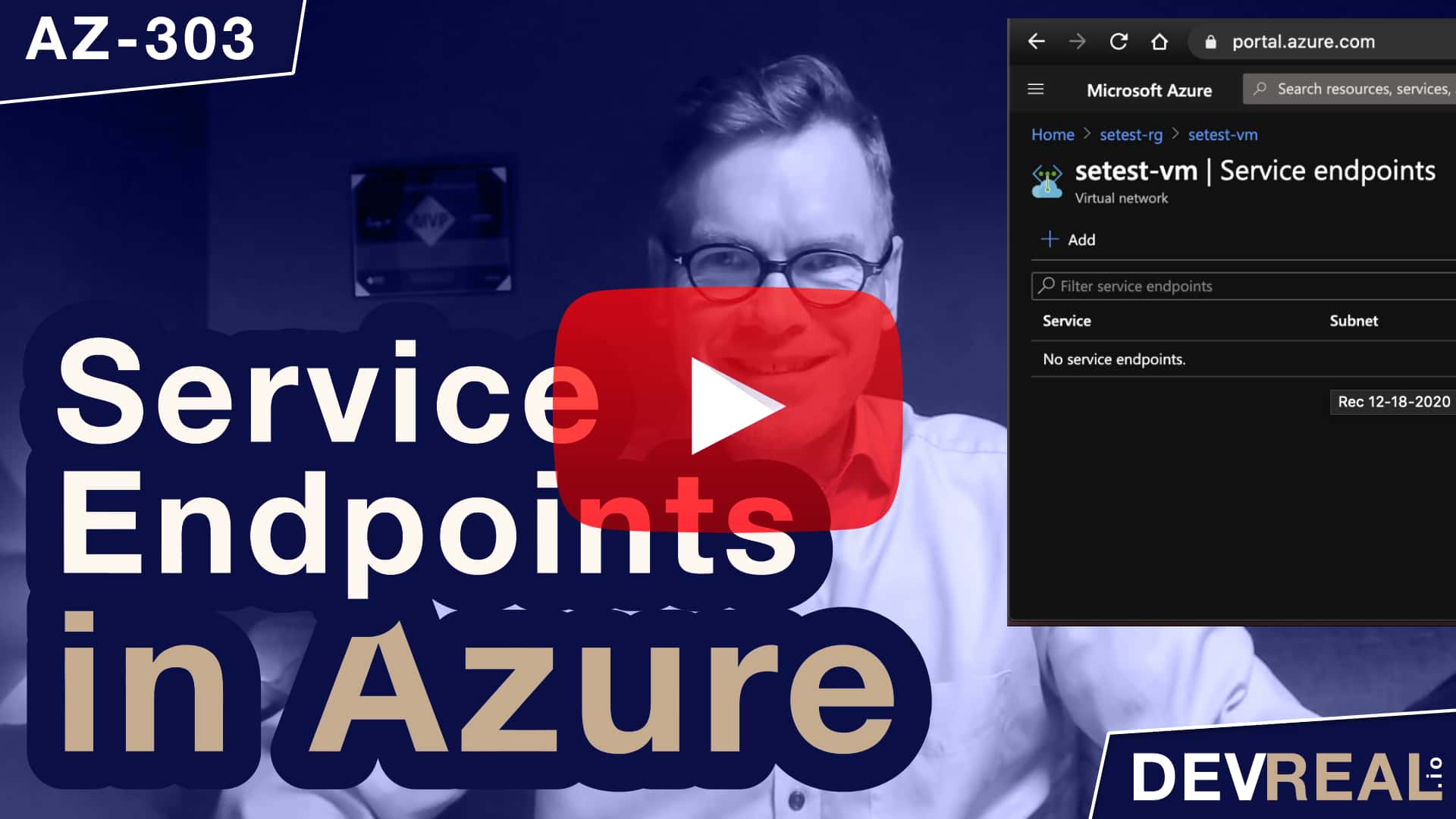 Watch Service Endpoints in Azure in preparation for the AZ-303 exam
Watch Service Endpoints in Azure in preparation for the AZ-303 exam
When we create an Azure Storage Account, and store items there, we can access them by using the URL that is provided to us. The traffic is then going over the internet. If we want to restrict the access to certain clients, we can route the traffic over the Azure backbone by using a service connection. It’s more secure and less latency.
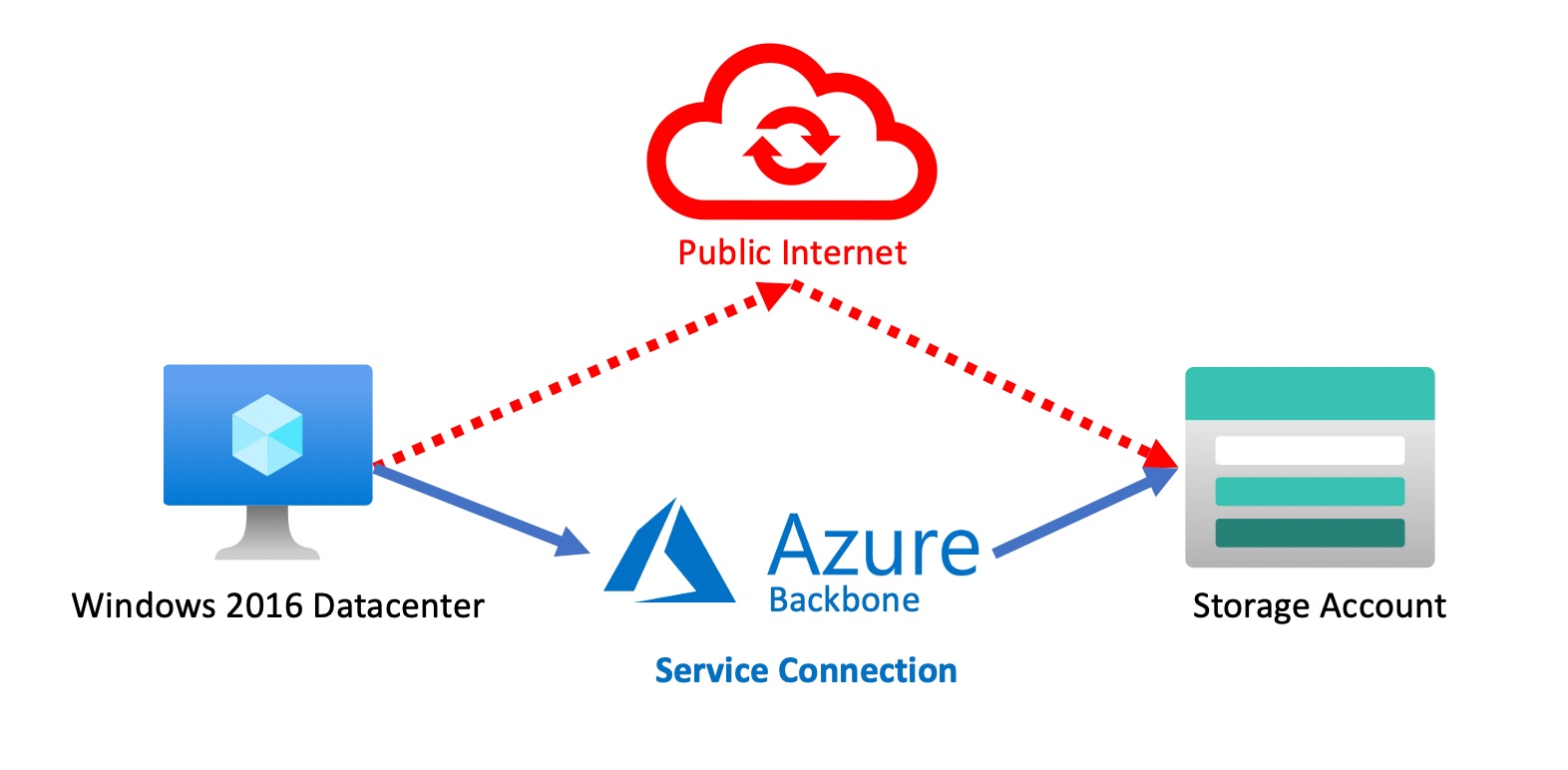 Diagram of Service Endpoints in Azure
Diagram of Service Endpoints in Azure
In preparation to this step-by-step guide, I already provisioned a few resources that we will need.
- Storage Account with container and an image
- Windows Server 2016 Datacenter Virtual Machine in VNet/subnet
- Azure Bastion and Public IP address
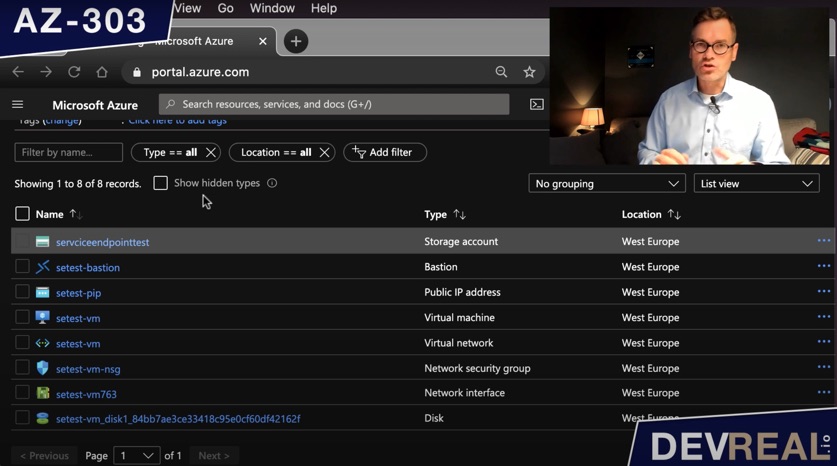 Service Endpoint Resource Overview
Service Endpoint Resource Overview
As you can see I have one image stored in the storage account.
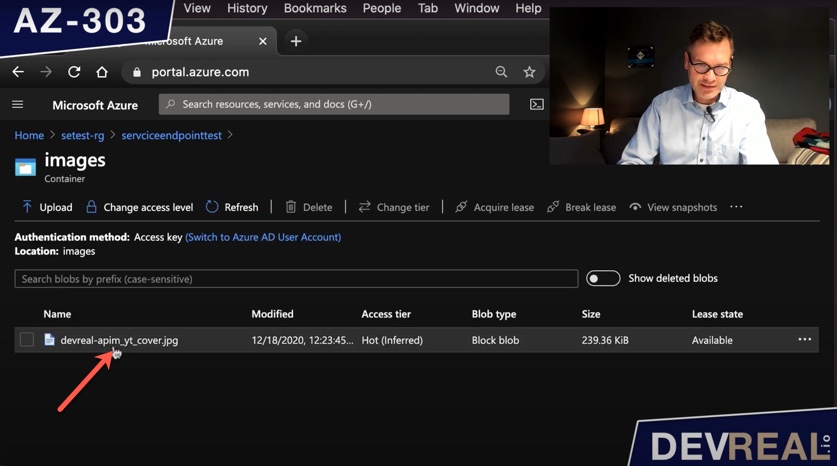 Content of container in Azure Storage Account
Content of container in Azure Storage Account
To show you that the traffic is going over the internet for now, I create an URL with a SAS token as the containers access level is private per default.
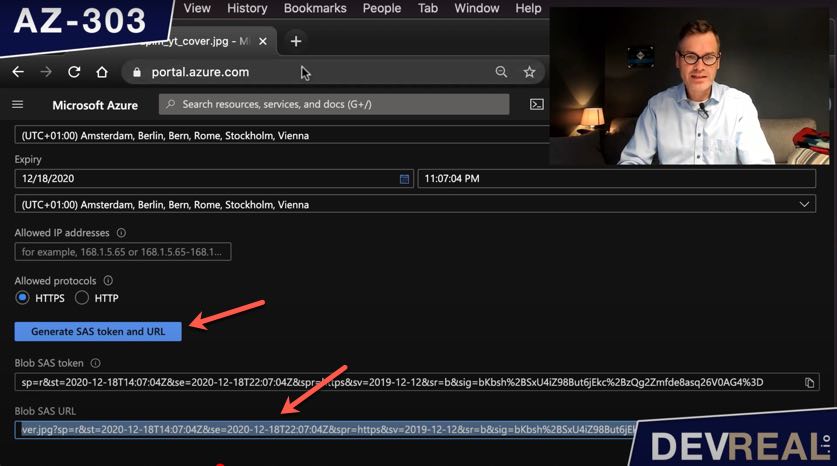 Create URL with SAS token for item in container in Azure Storage Account
Create URL with SAS token for item in container in Azure Storage Account
When pasting the URL into the browser of my workstation, you can see that it’s perfectly accessible.
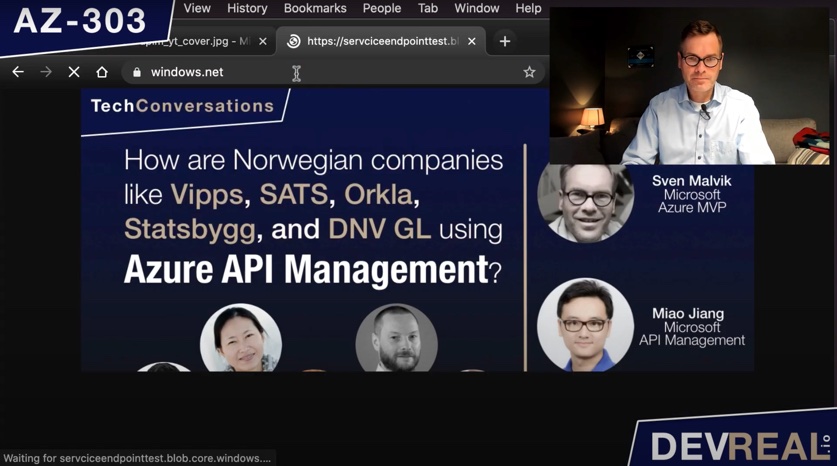 Accessing item in container in Azure Storage Account from workstation
Accessing item in container in Azure Storage Account from workstation
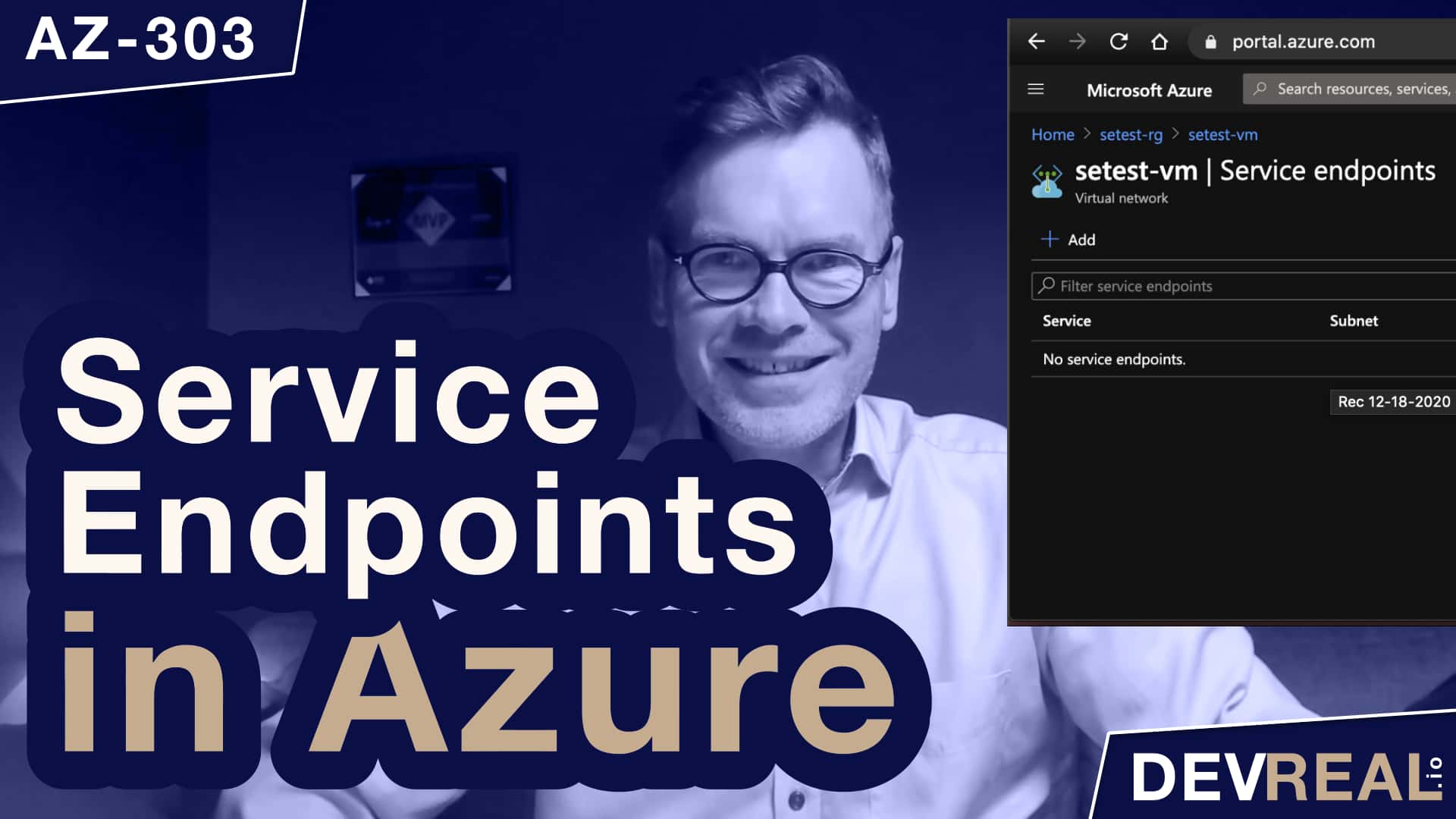
I’m now going to select Service endpoints in the virtual network of the Windows Server 2016 Datacenter VM.
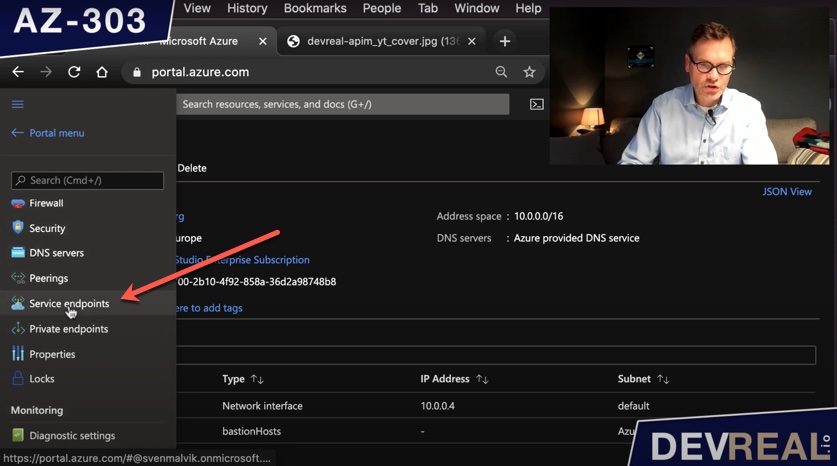 Service endpoints menu in virtual network
Service endpoints menu in virtual network
Click on Add to create a service endpoint and select the service Microsoft Storage and the subnet of the Windows Server 2016 Datacenter VM.
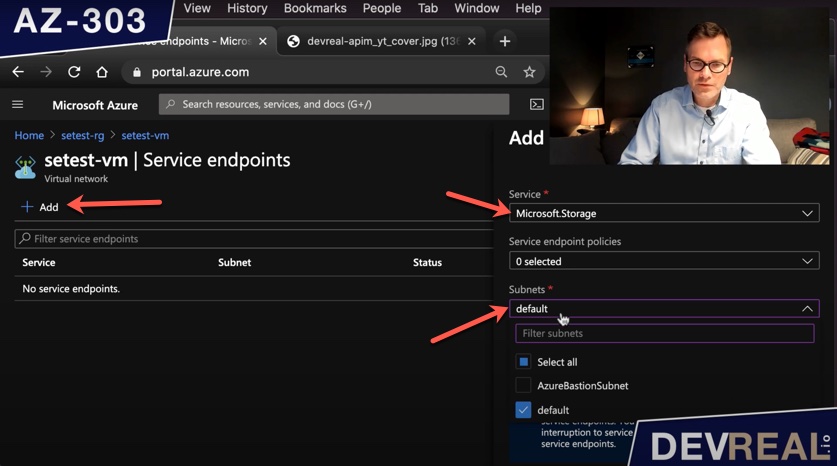 Adding a service endpoint to subnet
Adding a service endpoint to subnet
After creating the service endpoint for the subnet, you should see an entry in the overview of Service Endpoints.
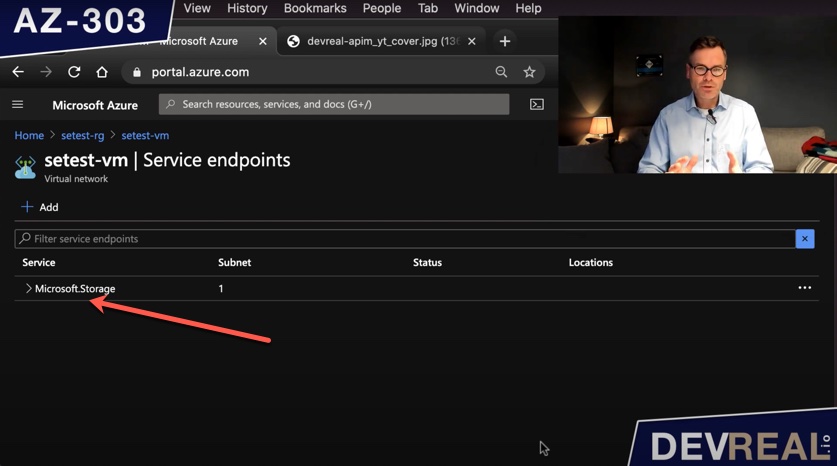 Overview of Service Endpoints
Overview of Service Endpoints
We head now over to the storage account, and select Networking. As you see, there is no virtual network selected for now which means that the content isn’t restricted to a location yet. To change this we select networks.
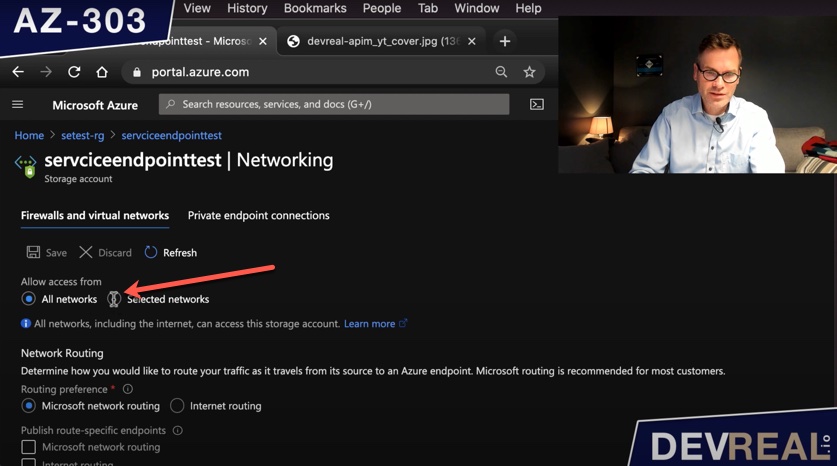 Starting restricting access to networks
Starting restricting access to networks
Now we can click on Add existing virtual network and select the subnet in which the VM is we would like to give access.
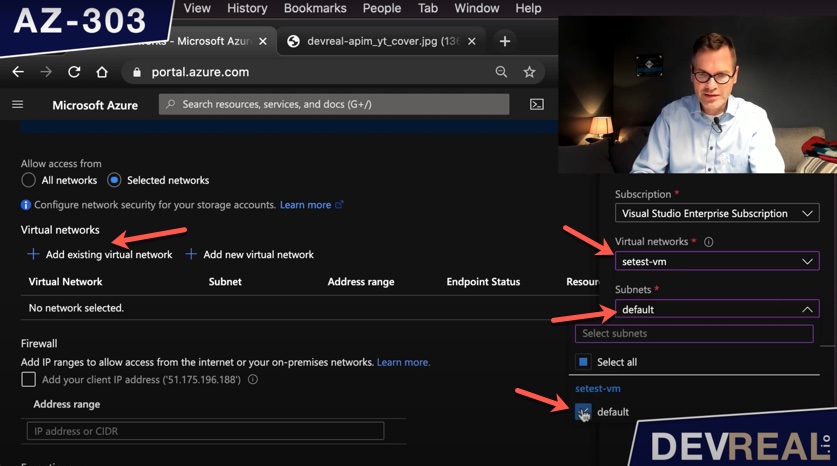 Restricting access to subnet for Azure Storage Account
Restricting access to subnet for Azure Storage Account
As we now have restricted the access to the Windows Server 2016 Datacenter VM, I am not longer allowed to access the content of the storage account from my own workstation.
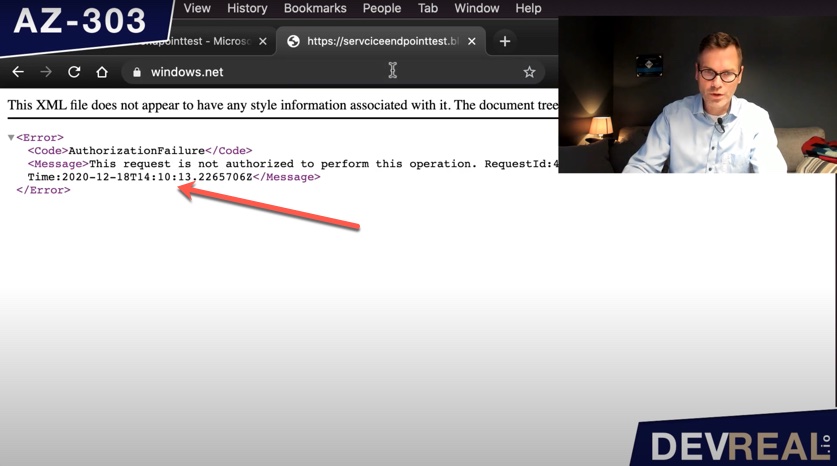 No access to Azure Storage Account
No access to Azure Storage Account
I use Azure Bastion to login to the Windows Server 2016 Datacenter VM.
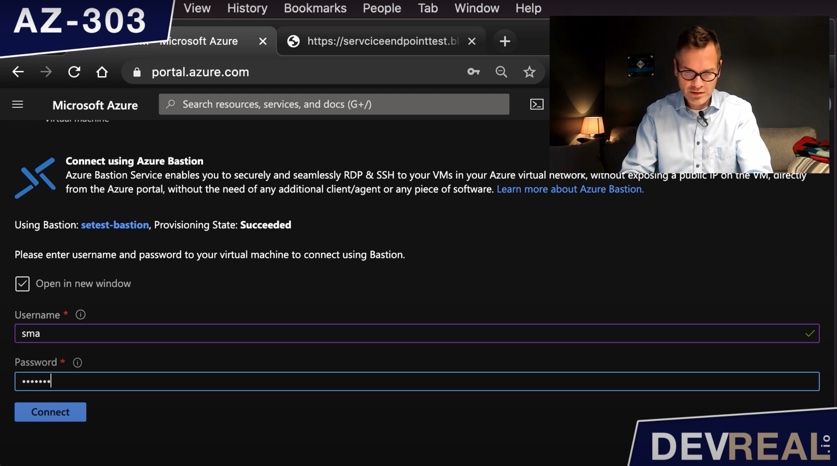 Login to VM with Azure Bastion
Login to VM with Azure Bastion
Vóila. We have access from the subnet where this VM is provisioned to.
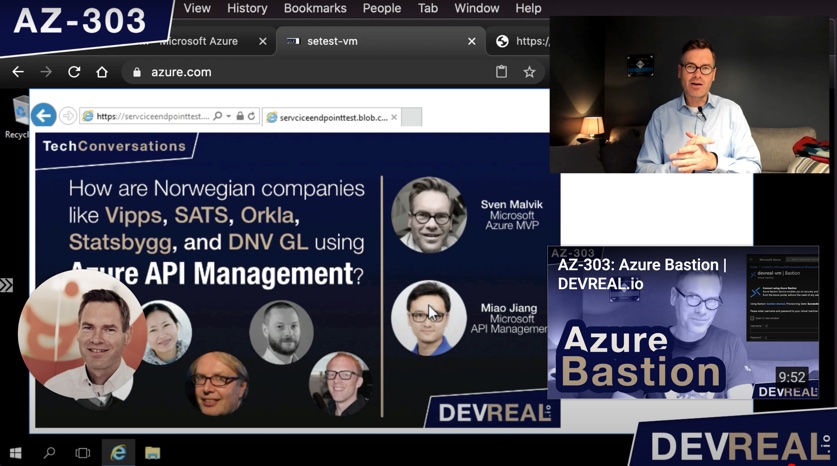 Access to Azure Storage Account
Access to Azure Storage Account
 Sven Malvik
Sven Malvik